Key findings
- There are 2,200 cyberattacks every day in the U.S.
- 1 cyberattack occurs every 39 seconds
- 95% of all digital breaches are caused by human error
- Phishing is the most common email attack method
- 2023 saw an 8% increase in weekly cyberattacks globally.
If there’s one thing we have learned about internet security, it’s this: It’s tough out there! Unfortunately, it seems to be getting worse. From popular sites like LinkedIn and diet-and-exercise tracker MyFitnessPal to game developer Zynga and dozens more, reported data breaches are making headlines more than ever.
According to the FBI’s 2022 Internet Crime Report, personal data breaches have grown in the past four years, accumulating $742,438,136 in victim losses. Cybercrimes are expected to keep increasing in numbers, too.
You may want additional security protections for many reasons, especially if you’re a freelancer who works outside the home. But first, let’s look at the most common types of threats.
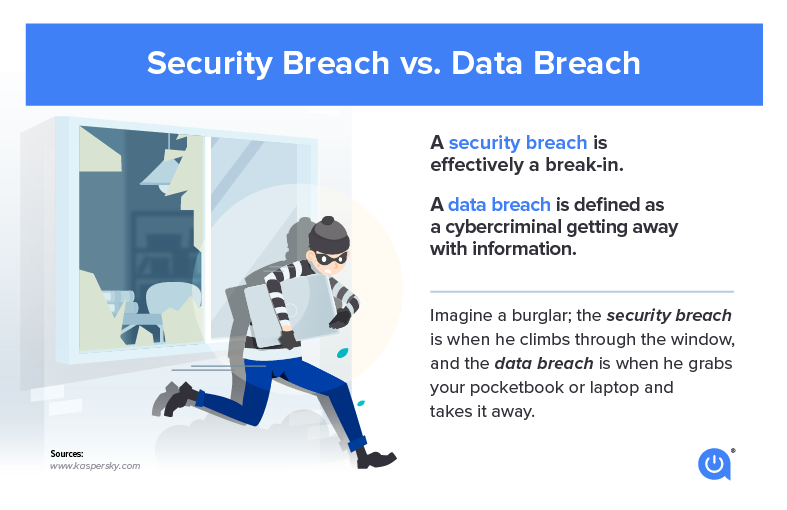
First of all, what is a breach?
A “breach” is an incident in which data is inadvertently exposed in a vulnerable system, usually due to software security weaknesses. A breach, therefore, results in information being accessed without authorization and occurs when someone can break through the system’s security.
Breaches allow hackers to obtain confidential and personal information, like credit card numbers for example, that are used for identity theft and fraud.
Types of internet security threats
Malware, worms and spam
According to security giant McAfee, malware, short for “malicious software,” comes in many forms, including different types of computer viruses, worms, “Trojans” and dishonest spyware.
Worms are software programs that duplicate themselves from one computer to another. Without human interaction, these copies can create themselves and spread rapidly in high volumes.
Spam refers to unwanted messages in your email inbox. We’ve all seen it: Junk mail advertising goods or services that we aren’t interested in, which, though annoying, are typically considered harmless. Some, however, when clicked on, can include links that install malicious software on your computer. Rude.
Trojans are a type of malware that hackers use to breach into a personal or business system. Trojans disguise themselves as harmless software but are actually malicious. They can appear as free software, videos or music or advertisements that look legitimate.
Phishing
Cybercriminals are sneaky. Through a process called phishing, they attempt to solicit private or sensitive information by posing as a familiar entity, like your bank or web service. If they sufficiently convince you, you may be tempted to click on links to verify details like account information or passwords.
Botnet
Infected with malicious software, a botnet is a network of private computers usually controlled by a single user and often prompted to engage in criminal activities like spam or denial-of-service attacks.
Password attacks
Password or brute-force attacks use authorization vulnerabilities to access and expose a user’s accounts. This involves the hacker using different password-attacking techniques to breach your device and personal accounts.
Ransomware
Ransomware is malware that encrypts files on a device, making the files and system unusable. The hackers then demand ransom in exchange for the decryption of the system. Essentially, the ransomware locks your computer until you pay the ransom fee. The most common way ransomware infects your device is by visiting malicious websites or downloading malicious attachments.
Man in the middle attacks
These attacks are breaches that allow criminals to intercept data transmitted between networks, computers or users. It’s sort of like eavesdropping on your internet activity.
So, how can you keep yourself safe?
First, be smart about secure browsers
Each web browser has its security measures, but some have flaws that allow hackers to invade. To check if the site you’re on is secure, look at the URL. If it begins with “https,” you’re in good shape because the site is secured, using an SSL Certificate.
If the website does not have “https,” that means any data passing through your system is insecure. This is especially important for transactional sites involving information like credit card numbers, so be sure to check the URL for “https” before entering any personal information.
Check 1, 2: Is it really you?
To prove you are you, multi-factor authentication works to control access by requiring several types of evidence. Send a text to your mobile device to ask for security questions; you’ve seen it before: Websites and email accounts can be made more secure by requiring at least two factors of authentication. You could also check your email or social media account settings for multi-factor authentication options.
Protect your email accounts
Ah, email. We can’t live without it these days, but email, unfortunately, creates a ton of chances for viruses, worms and other malicious programs to enter our systems. Email messages can be protected using cryptography, which creates codes that keep your information secret.
Also, be sure to have strong, secure passwords that are less likely to be breached. You could also try using apps like 1Password or LastPass that store passwords and digital records for extra security.
Use a VPN
A VPN is a great way to add extra security to your systems. A VPN stands for Virtual Private Network and allows you to browse the internet anonymously, giving you extra security on your network. It essentially encrypts your internet activity, so no one can see what you’re doing online, which is appealing for those handling sensitive information. There are tons of VPN options available, both free and paid, so check out our list of the best VPNs.
Update your operating system and software
Software updates can prevent many security issues and are necessary to keep your devices running smoothly and without glitches. There are constantly new security updates available, and you should make sure you’re updating your systems accordingly to ensure you have the latest security updates installed.
Monitor young users
Invest in good security like Norton or Kapersky. Every security app or program offers parental controls, such as website blocking, to keep your child and your information safe. Students can also benefit from safety guides when accessing the internet for classes and research.
ISPs with internet security
Many internet service providers (ISPs) offer additional levels of web protection. Check first to find out what yours offers, and then, you may want to opt into additional layers of security.
Xfinity xFi Advanced Security offers security measures for all your devices, from computers and phones to security cameras and smart thermostats. It is available at no extra cost for Xfinity Internet subscribers who also rent a compatible xFi gateway device. xFi can help you avoid risky sites, block remote access to your smart devices from risky sources, monitor devices in real-time and alert you when your devices are behaving in unusual ways.
Verizon Internet Security Suite offers a robust array of services, from McAfee Active Protection (against malicious threats), real-time protection against virus attacks, secure firewall protection and even parental controls — for all devices using Verizon’s service.
Spectrum offers a downloadable security suite for Business Internet users at no additional cost. The suite software offers protection against malicious software, including viruses, spyware, worms, Trojans and more. Through the firewall feature, allow only safe internet connections and block unwanted access to your computer.
Hughesnet allows you to add on a Norton 360 Deluxe package for $6 or $7/mo, depending on the number of devices you want to cover. It includes parental controls, dark web monitoring, a webcam safety app and a password manager.
All of AT&T’s fiber plans come with ActiveArmor security, which monitors your devices through a safety scan, protects your network 24/7 from malicious threats and monitors your personal information for any breaches.
When in doubt, ask your provider what they offer and what you can do to further their existing protections. Now that you know a little more about the threats in the internet world, you can be more diligent about protecting yourself. Keep connected to our Resource Center and be sure to stay safe out there!
Cyber attack FAQs
What are the most common type of cyberattacks?
Phishing emails are the most common threats, often camouflaged as services you are familiar with to get your personal information.
What are the cybersecurity terms used to describe the two types of insider threats?
There are intentional and unintentional threats. Intentional threats are done on purpose by an insider, like an employee, to gain revenge or money. Unintentional cyber-threats occur through negligence on someone’s part, like clicking on an unknown link or not updating system software, etc.
How can I stop cyberattacks on my devices?
A few practices can keep your personal information and devices safer. Turn on Multifactor Authentication when available. You can also use a password manager. Take advantage of your ISP’s internet security package if offered.
Allconnect: Let us compare providers for you
Why should you choose Allconnect? We’re the #1 broadband marketplace in the U.S, meaning you can trust us to search, compare and order internet and TV service for your home.
Get started
Written by:
Robin LaytonEditor, Broadband Content
Robin Layton is an editor for the broadband marketplace Allconnect. She built her internet industry expertise writing and editing for four years on the site, as well as on Allconnect’s sister site MYMOVE.com. …
Read more

Edited by:
Anine SusEditor I
-
Featured
![How does the internet work?]() How does the internet work? AJ Dellinger — 6 min read
How does the internet work? AJ Dellinger — 6 min read -
Featured
![Have a good internet speed for gaming? What you need to win your online battles]() Have a good internet speed for gaming? What you need to win your online battles Taylor Gadsden — 7 min read
Have a good internet speed for gaming? What you need to win your online battles Taylor Gadsden — 7 min read -
Featured
![How to secure your home internet connection]() How to secure your home internet connection AJ Dellinger — 5 min read
How to secure your home internet connection AJ Dellinger — 5 min read
Latest
-
Wednesday, October 23, 2024
What is my IP address and why does it matter?Camryn Smith — 3 min read
-
Tuesday, October 22, 2024
Everything you need to know about internet speedsRobin Layton — 5 min read
-
Tuesday, October 22, 2024
How to change your Wi-Fi network passwordCamryn Smith — 3 min read






